

Today Rocio, a friend of Esme, visited us to pick up her share of the mangos we picked up last Sunday on our walk near the town of Buenavista. Also she wanted to copy some files from Esme's computer so she had brought a USB flash drive with her.
Esme's computer was booted into Ubuntu Linux. I had installed this operating system the 26th of June, 2007 on a new 80G hard disk drive, which I had made the primary drive of her computer. The old 40G hard disk drive with a Spanish version of XP had become the secondary drive. Since the files Rocio wanted resided on the 40G hard disk, I mounted the drive within Ubuntu, and inserted the USB Flash drive into the computer. This all seemded to work fine, however, some files had weird characters in their filenames. I was not sure if this was caused by accented characters or that something else was wrong, so I decided to copy the files in a shared folder on Esme's computer, and copy those shared files on my computer to Rocio's USB flash drive.
When Esme inserted the USB stick in my computer and opened the drive by double clicking on its icon in My Computer, a message popped up:
adp failed to set date for 'Notepad'
When I saw this, I repeated what she did, and there was that message again. Something on the USB flash drive was being executed after the drive icon was double clicked, and somehow it failed to set the date for 'Notepad'. When I examened the folder of the USB drive I didn't see any weird file. So in the "Tool" menu of the folder window I selected "Folder Options...". This opened the "Folder Options" dialog window. Then I clicked on the "View" tab and enabled "Show hidden files and folders".
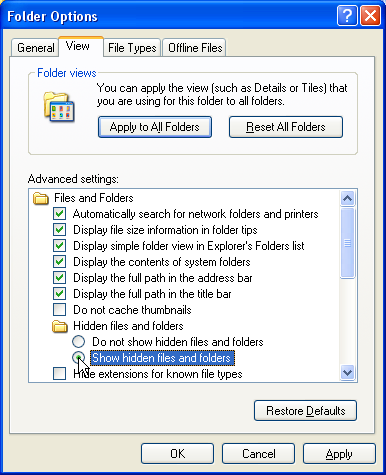
Now I could see the two files that had been made hidden on Rocio's USB flash drive: Autorun.inf and adp.exe. The former caused adp.exe to be automatically started as soon as the flash drive was opened via My Computer.
The next question was: what is adp.exe. I already suspected it to be a piece of malware and a search for adp.exe with Google confirmed this:
Adp.exe is a spyware process that is installed with VOIP (voice over IP) and file sharing software, for example Net2Phone, Grokster and KaZaa.
adp.exe is considered to be a security risk, not only because spyware removal programs flag ADP as spyware, but also because a number of users have complained about its performance.
Source: adp.exe - ADP, Spyware Notice!
Another page I found with Google named the threat VCatch:
This threat copies its file(s) to your hard disk. Its typical file name is VCatch. Then it creates new startup key with name VCatch and value adp.exe. You can also find it in your processes list with name adp.exe or VCatch.
Source: VCatch and adp.exe - solve this problem now!
The page offered a program that fixes this issue, but since I had no idea if I could trust the site or the program it offered for download, I decided to read the instructions on the same page for manual removal. Based on the information I was lucky: I my personal acount has limited rights and hence the malware hadn't been able to copy itself to C:\Program Files\. I searched in the registry, but it had also not been able to nestle itself into the registry.
Next I copied Rocio's file to a newly created folder on my hard disk, logged into an account with Administrator rights and formatted the USB stick (carefully not to open it while I had Administrator rights). When I logged back into my personal limited account I checked the USB stick and ... again it contained adp.exe and Autorun.inf. So I pressed Ctrl+Shift+Esc simultaneously to open the Windows Task Manager, clicked on the Processes task, selected adp.exe in the list, and ended the process.
Then I formatted the USB Flash drive again the same way as described above, and logged back into my personal account, and ... again the two files were back. I checked again the list of running processes in the Windows Task Manager and noticed another instance of adp.exe running, which I killed as well. And finally, after another format of the USB drive, the malware was finally gone.
While I was trying to remove the virus, Rocio was feeling quite guilty, and I was feeling quite stupid. I have been using computers since 1984 and should have been more careful. Twice before I had come close to getting a virus, on both occasions thanks to an infected floppy disk. But that had been over 10 years ago. Yet I should have known better, especially since I often call the USB Flash drive the perfect floppy replacement - well, actually not so perfect because all three USB Flash drives Esme and I own don't have a write-protect switch...
Anyway, I was sure that Rocio's computer had been infected as well since I am afraid she, like a lot of other Microsoft Windows users, uses an account with Administrator rights all the time. Sadly this (almost) needed to make some applications work on Windows - and if you complain about this behavior the makers state that their software is written that way, because people run everything with Administrator rights. Right! Incompetent software developers? Yes, without a single doubt.
Rocio asked me how to clean up her computer, so I browsed to the Portable Apps website and downloaded the portable version of ClamWin antivirus which I installed on her freshly formatted USB Flash Drive. I ran the program from her flash drive, and after it had downloaded the latest virus definition files, I let it scan the flash drive. And surprise: no viruses or other malware found. I recommended her to scan her own computer with this wonderfull portable program as well, and warned by this all, decided to check out Esme's and my own USB flash drives as well. At least two had been used to transport files to shops for printing.
G:\>ls -al *
-r--r--r-- 1 user group 34 May 9 2006 Autorun.inf
-r-xr-xr-x 1 user group 1211 May 12 2006 copy.exe
-r-xr-xr-x 1 user group 70207 May 20 2006 host.exe
-rw-rw-rw- 1 user group 525071 Jul 4 17:15 robberfly.jpg
ClamWinPortable=:
total 117
drwxrwxrwx 1 user group 0 Jul 17 20:18 .
drwxrwxrwx 1 user group 0 Jan 1 1980 ..
drwxrwxrwx 1 user group 0 Jul 17 20:18 App
-rwxrwxrwx 1 user group 110496 Mar 13 08:52 ClamWinPortable.exe
drwxrwxrwx 1 user group 0 Jul 17 20:19 Data
drwxrwxrwx 1 user group 0 Jul 17 20:19 Other
-rw-rw-rw- 1 user group 8316 May 30 16:10 help.html
G:\>md5sum *
2b53df81ad082193659e9a37b28f173b *Autorun.inf
md5sum: ClamWinPortable: Permission denied
f7bd87b88e591e4ac9b3553852740984 *copy.exe
1d4c07370babee309401a73ebaa64f58 *host.exe
3d522fb6702b75b171fe2abc4ff90b2e *robberfly.jpgBoth 2GB flash drives turned out to be clean, but Esme's 256 MB USB flash drive contained three very suspicious files: Autorun.inf, copy.exe, and host.exe. I installed ClamWin antivirus on her USB stick as well, and ran the program.
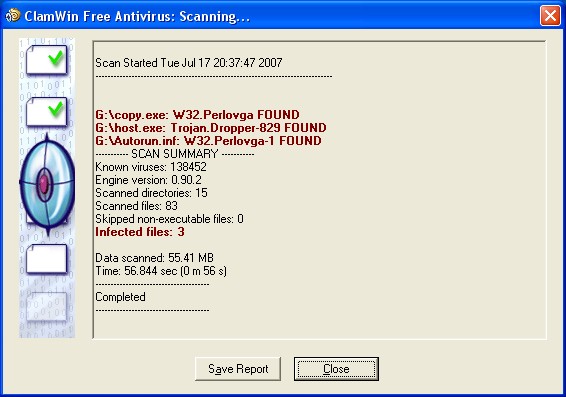
As expected, ClamWin antivirus confirmed my suspicion: malware. I deleted the three files, and decided to let my computer on so the program could scan both hard drives, and two inserted USB sticks again.